In Salesforce, you are able to manage security assurance levels to control what a user has access to within Salesforce.
This can be useful if you to lock down specific areas within Salesforce. For example, who is able to access reports, export and print reports, to managing users, user unlocks and password resets.
Changing assurance levels at Organisational level and Profile levels
We can choose to set and manage Security assurance levels at organisational (org) and profile levels in Salesforce.
In Salesforce, there are essentially two security assurance levels that can be set:
|
Salesforce assurance levels |
|---|
| HIGH ASSURANCE |
| STANDARD |
Using these Security assurance levels in Salesforce, it is possible to create a scenario where users who log in through from an Identity Provider (such as Okta) and they are automatically granted "high assurance" access within Salesforce. Moreover, Salesforce does not require them to provide an additional verification method such as Salesforce Authenticator/ MFA.
Configuring assurance levels at Organisational level and Profile levels
So in the next sections, I will explain how you can configure the assurance levels, and what access the assurance levels gives.
That is:
- Changing assurance levels at Org level in Session Settings
- Changing assurance levels at Profile level in Profiles
- Changing what assurance level means in Salesforce
- Testing that it works
I will use Okta SSO as the example authentication option, where logins from Okta SSO = High assurance.
Changing assurance levels at Org level in Session Settings
So let's assume you have configured Okta Single Sign On (SSO) as authentication providers in your site.
You want users who log in via their Okta SSO account to be automatically granted high assurance access and bypass additional verification such as Salesforce MFA.
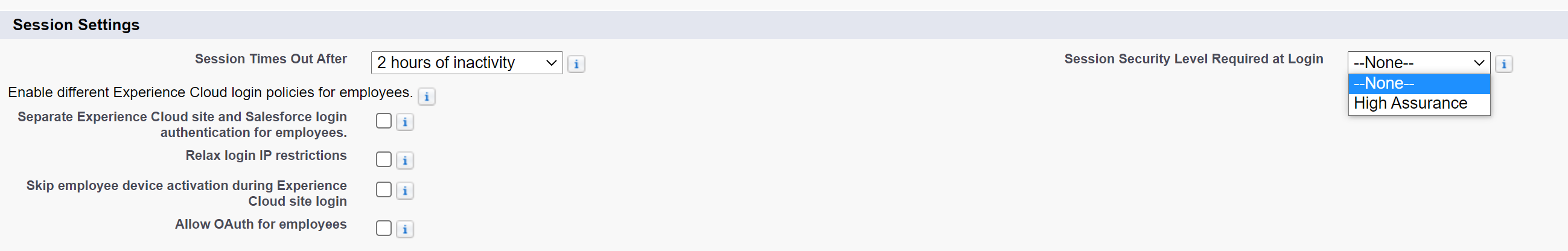
To do this, we need to go the User profile, set the session security level required at login to "High Assurance".
1. Go to Setup> Administer > Security Controls> Session Settings
2. On the "Session Settings" page, scroll down to "Session Security Levels".
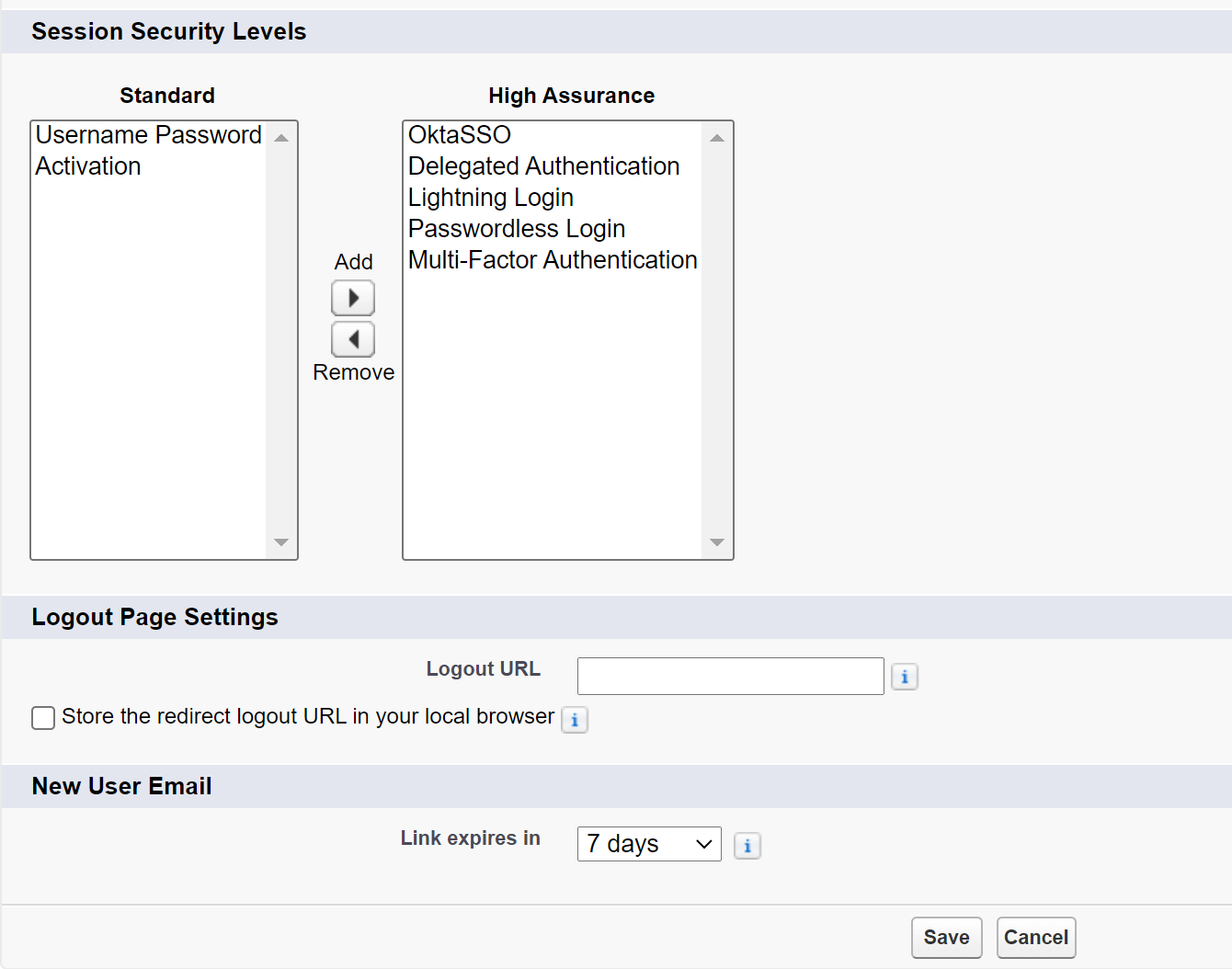
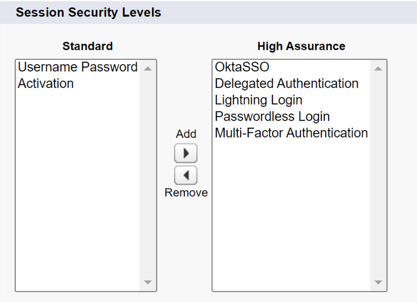
3. You will see two columns here, "Standard" and "High Assurance", where:
- Standard column - anything that you want to require MFA before granting user access to the section in Salesforce, put in the "Standard" column.
- High Assurance column - Add Multi-Factor Authentication to the High Assurance column.
For example, with "Username Password" in the Standard column - When users log in with their Salesforce username and password, they’re required to provide a verification method (e.g. MFA) before being able to log in.
For example, with "Okta SSO" in the High Assurance column - When users log in with their Okta SSO account, they’re granted High Assurance access without needing to provide a verification method.
Changing assurance levels at Profile level in Profiles
Assurance levels can also be changed not just at the device level and organisational level but at the profile level.
When a user logs in from a High Assurance authentication source and specific Profile, they will be automatically tagged as a High Assurance user in Salesforce.
1. Go to Setup> Administer > Manage Users> Profile> click on any profile
Or you can go to Setup> Quick Find box and search for "Profiles".
2. Click any profile name you want to edit.
3. Then click Session Settings.
 Click Edit
Click Edit
4. Scroll down to Session Settings.
Here under the "Session Security Level Required at Login", we can change this to High Assurance, then click Save to save your changes.
Changing the assurance levels in Salesforce
We can change what the security assurance levels means in Salesforce by updating "Session Security Level Policies".
Step 1 - Open "Identity Verification" on Salesforce
In Salesforce, go we will need to go to "Identity Verification".
Setup> Administer> Security Controls> Identity Verification
An easy way to find it is to search "Identity Verification" in the "quick find" box.
Step 2 - "Identity Verification" set up on Salesforce
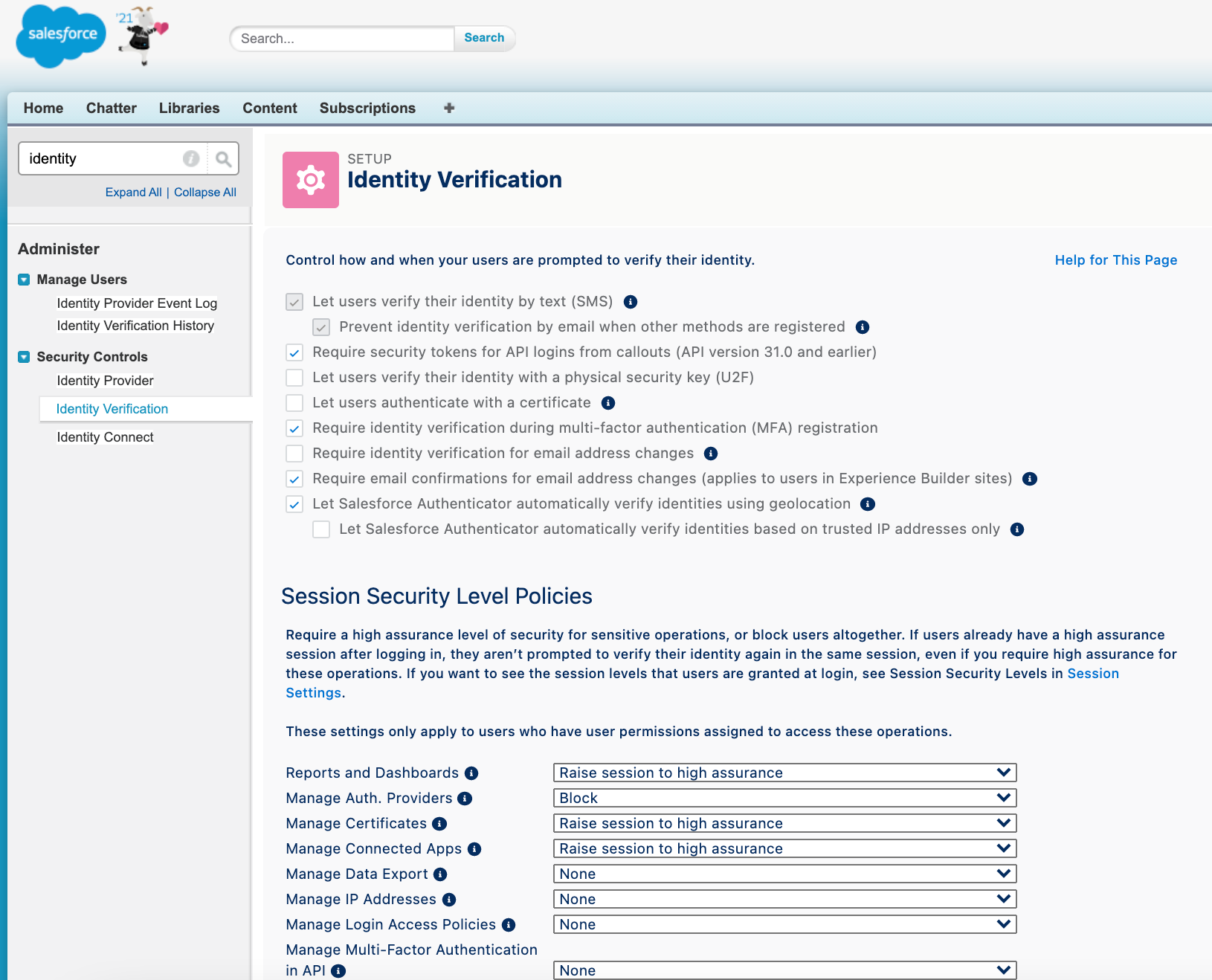
You will then be presented a page where you can configure identity vertification settings and sensitive operation flags.
Step 3 - Configure "Session Security Level Policies" on Salesforce
If you scroll down, you will reach a section called "Session Security Level Policies". It will say:
Require a high assurance level of security for sensitive operations, or block users altogether. If users already have a high assurance session after logging in, they aren’t prompted to verify their identity again in the same session, even if you require high assurance for these operations. If you want to see the session levels that users are granted at login, see Session Security Levels in Session Settings.
Session Security Level Policies
Using Session Security Level Policies you can tailor specific operations that a user can have based on their security assurance level tag that we have tagged with through Organisational level or Profile level settings in Salesforce.
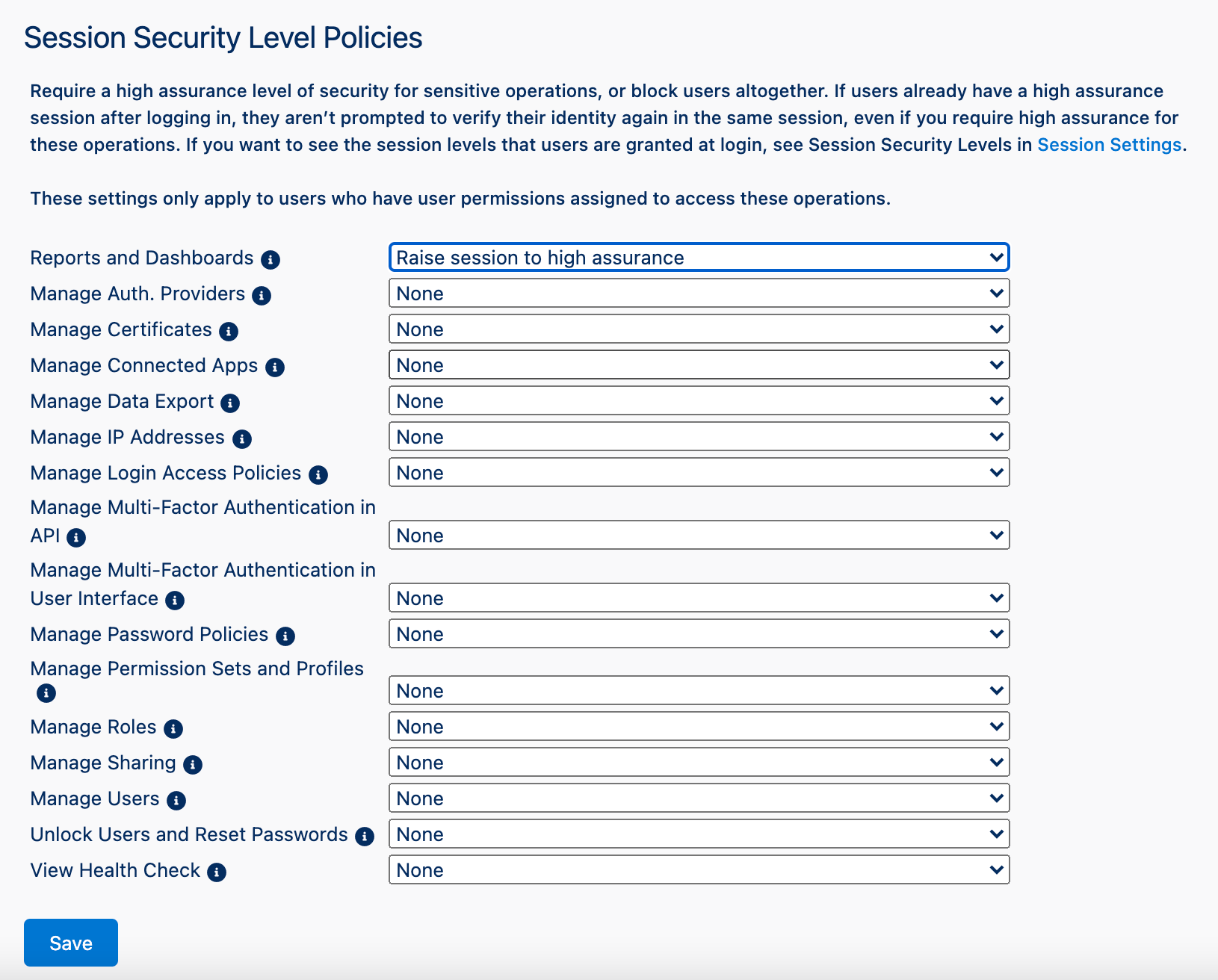
Under Session Security Level Policies, you can raise the session security level to high assurance, or block users.
To do so, click on any of the top down menus next to the item and you will get these options:
- None
- Block
- Raise session to high assurance
- (For Reports and Dashboards only) Raise session to high assurance when exporting or printing
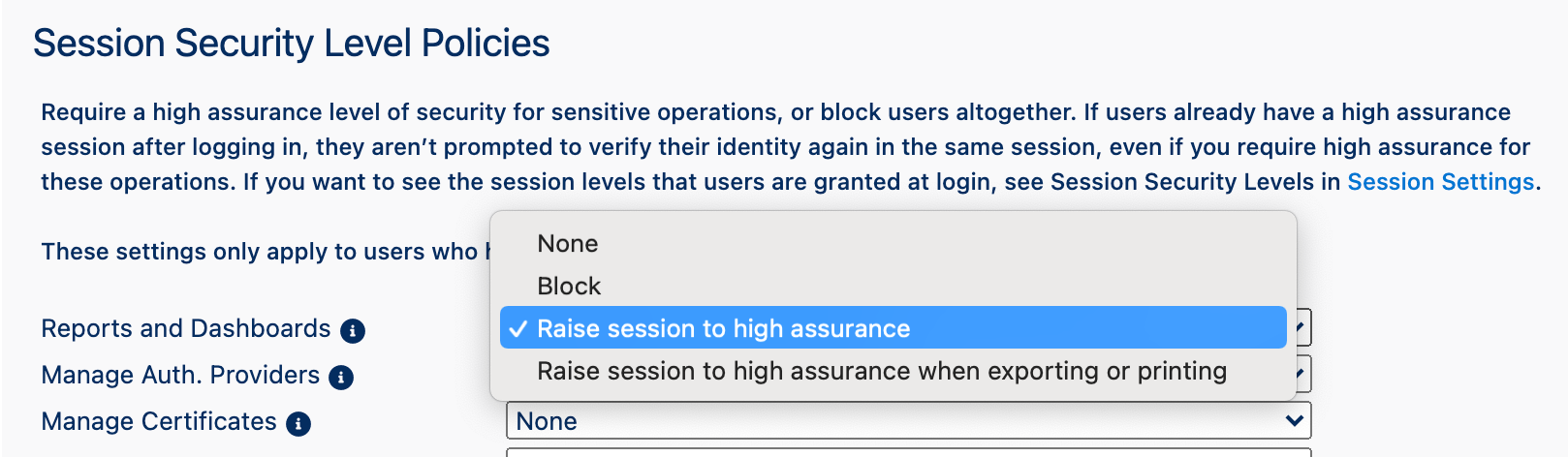
Here's an example, configuration setting. You can tailor this to your preference to testing.
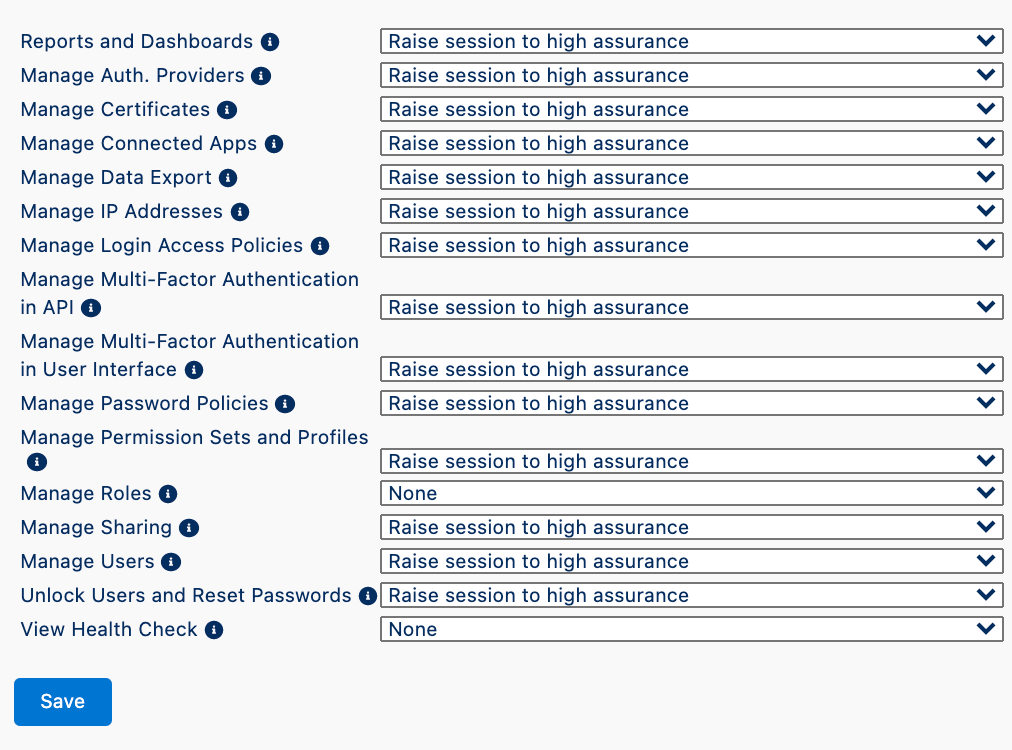
For context, this is what each item means, as noted in Salesforce's documentation.
- Reports and Dashboards—Controls access to reports and dashboards. This setting is also available on the Reports and Dashboards Access Policies page. You can change this setting in either location.
- Manage Encryption Keys—Controls access to the Platform Encryption page, the Certificate and Key Management Setup page, and the TenantSecret object.
- Manage Auth. Providers—Controls access to the Auth. Providers page, the User Details Setup page, and the AuthProvider object.
- Manage Certificates—Controls access to the Certificate and Key Management Setup page, Single Sign-On Settings Setup page, and the Certificate object.
- Manage Connected Apps—Controls access to the Connected Apps Setup pages and the App Manager Setup page.
- Manage Data Export—Controls access to the Data Export Setup page.
- Manage IP Addresses—Controls access to the Network Access Setup page.
- Manage Login Access Policies—Controls access to the Login Access Policies Setup page.
- Manage Password Policies—Controls access to the Password Policies Setup page and profile details.
- Manage Permission Sets and Profiles—Controls access to the Permission Sets and Profile Setup pages and related objects.
- Manage Roles—Controls access to the Roles Setup page, the UserRole object, and the Role object in Metadata API.
- Manage Sharing—Controls access to the Sharing Settings Setup page, the SharingRules object, and the CustomObject’s sharingModel field in Metadata API.
- Manage Multi-Factor Authentication in API—Controls access to the VerificationHistory, TwoFactorInfo, and TwoFactorTempCode objects.
- Manage Multi-Factor Authentication in User Interface—Controls access to the Identity Verification History Setup page and the VerificationHistory, TwoFactorInfo, and TwoFactorTempCode objects.
- Manage Users—Controls access to the Users Setup page.
- Unlock Users and Reset Passwords—Controls permission to reset passwords and unlock users on the Users Setup page.
- View Health Check—Controls access to the Health Check Setup page.
4. Test that is working
Based on whether you set up the assurance levels at the org or profile level, we can test if it is working.
|
Salesforce assurance levels |
|---|
| HIGH ASSURANCE |
| STANDARD |
Essentially what should happen is:
- When a user is tagged they should have access to anything tagged as "High assurance" required.
- When a user is tagged as a normal "standard" user, if they try access anything tagged with "High assurance" required, then they will be prompted for additional verification.
Org level tests
If it is at the org level, when a user log into Salesforce with username and password, they should get prompted for additional verification, i.e. Salesforce MFA, before being given access to Salesforce. If they access anything tagged with "High assurance" required, then they will be prompted for additional verification.
When a user logs in via Okta SSO, then they should not be prompted for any additional and be given access to Salesforce. They should also have access to anything tagged as "High assurance" required.
Profile level tests
Similar to the org level tests, however, it will be based on the user logging in and the profile that has been set for that user.
Assuming that are using the profile that we have set, then the user would be tagged as "High assurance".
When a user is tagged (via their profile) they should have access to anything tagged as "High assurance" required.
When a user is tagged (via their profile) as a normal "standard" user, if they try access anything tagged with "High assurance" required, then they will be prompted for additional verification.



