- Simulate: Logs the event and does not block or challenge the visitor (you can still decide to set to a block or challenge after review of the event).
- Block: Block will block visitors from that IP from accessing the site.
- Challenge: Will display a challenge (captcha) page before the visitor can enter the site.
How to set your Cloudflare to simulate firewall events
Step 1 - Go to the "Firewall" tab
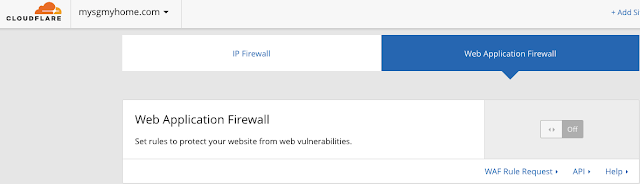
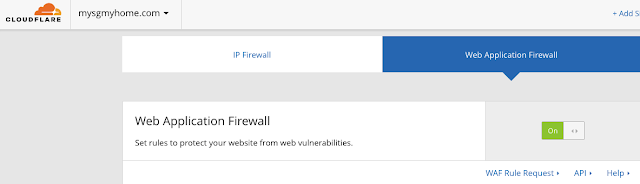
Step 2 - Click on the "Web Application Firewall" sub tab
Step 3 - Make sure your Web Application Firewall is set to Off
As we are simulating firewall events, let's first make sure your Web Application Firewall is set to Off. This is set to "Off" by default, so you can customise and switch it on when you are ready.
Step 4 - Let's review your Web Application Firewall settings and set to Simulate
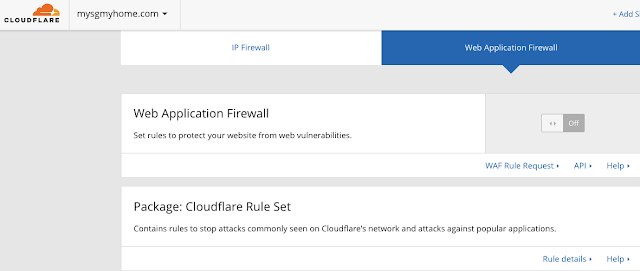
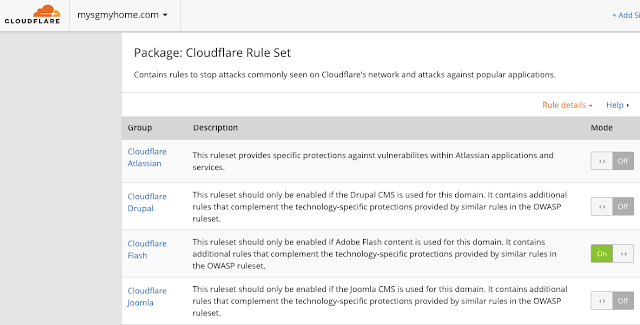
Step 4.1 - Review your "Package: Cloudflare Rule Set"
Let's review your "Package: Cloudflare Rule Set". You will be able to review when you click on the "Rule Details" link. It'll expand and give you a list of the rule groups you can switch on/ off.
If you get stuck and can't find it, copy this link below and put in your domain here.
https://www.cloudflare.com/a/firewall/YOURDOMAIN.com/waf#
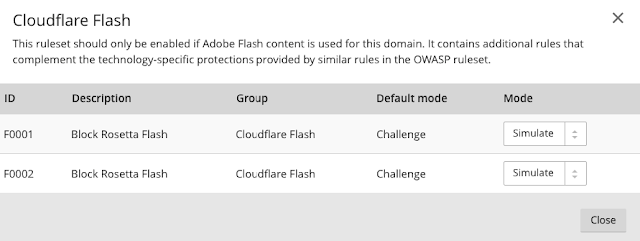
Step 4.2 - Review "Package: Cloudflare Rule Set" Rule Details
Step 4.3 - Explore the ruleset groups to deep dive and configure
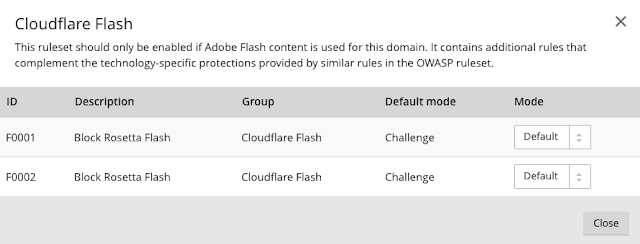
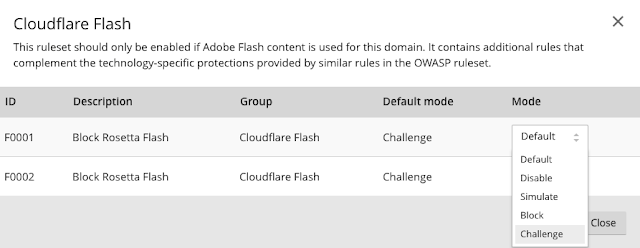
Step 4.4 - Configure your Cloudflare settings for your rulesets
- Simulate: Logs the event and does not block or challenge the visitor (you can still decide to set to a block or challenge after review of the event).
- Block: Block will block visitors from that IP from accessing the site.
- Challenge: Will display a challenge (captcha) page before the visitor can enter the site.
- Disable: Will simply turn off this particular rule
Step 5 - Review the OWASP ruleset package as well
Next, review the "Package: OWASP ModSecurity Core Rule Set" and configure it accordingly. For starting off, you can start with the simulate mode to get things started.
What is OWASP?
This package consists of rulesets derived from the OWASP ModSecurity Core Rule Set. These provide an easily pluggable set of generic attack detection rules that provide a base level of protection for any web application.
The OWASP rules operate in scoring threshold mode: each match against a rule increases the threat score of that request. Once a request exceeds a configurable sensitivity threshold (off, low, or high), the action is taken. This action can be simulate (create a log entry but do not block the request), challenge (present the user with an in-browser challenge page, and log), or block (reject the request and log).
Individual rule groups within the OWASP package can be enabled or disabled in "rule details", after which rules can be managed at the individual rule level through the advanced option.
Step 6 - When you are ready, switch your Web Application Firewall is set to On
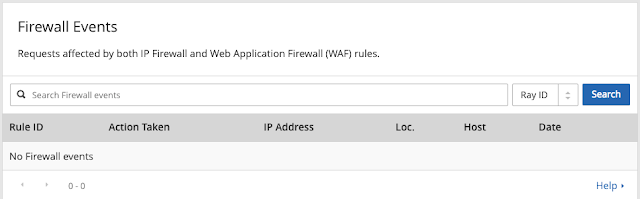
Step 7 - Review the Web Application Firewall results
Under the "Traffic" tab. You can scroll down until you see the "Firewall Events" section. This is where you will find the simulated, challenged firewall events.
Step 8 - Review and update settings
Keep iterating and reviewing settings until you are comfortable.